TRUSTED BY BOEING, HONEYWELL AND AIRFORCE. ITAR/HIPPA COMPLIANT
Stay Connected
Slack channels for developer relations
High-Uptime
X
99.97% and response time promise in Service Level Agreement.
Reliability
Operational for 12+ years. Trusted by big brands.
Dont Dwell on Data Leakage
When your documents are being shared via email, teams and countless folders, you have no idea where they could end up. Our customers no longer have this insecurity. All their files can be stored safely in Threads.
Role-Based Access Control
-
Granular Permissions: Users are assigned roles (e.g., operator, manager, admin), each with different levels of access to sensitive data or features.
-
User Authentication: Controls who can access specific threads, documents, or workflow data, preventing unauthorized personnel from viewing sensitive information.
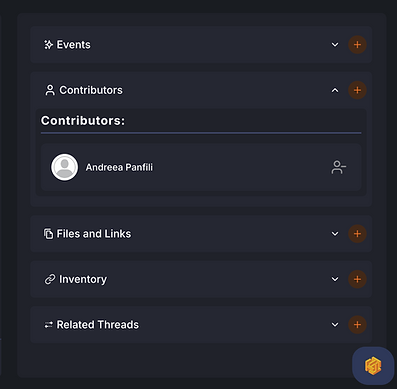



Secure File Sharing
-
Controlled Sharing: Limits file access to specific users or groups, ensuring that sensitive manufacturing files or designs are shared only with authorized personnel.
-
File Version Control: Tracks changes to files and ensures the latest secure version is being used, preventing accidental use of outdated or compromised data.
Audit Trails and Activity Logs
-
Detailed Logs: Every user action (file access, modifications, thread participation) is logged to track who accessed what and when.
-
Compliance and Accountability: Helps ensure compliance with industry standards (e.g., ISO, ITAR) and holds users accountable for their actions within the system.


Secure Collaboration Channels
-
Private and Encrypted Communication: Ensures that all communication within threads (chat, comments, file sharing) is secure and private, visible only to authorized users.
-
Tamper-Proof Messaging: Prevents modification of communication records to ensure that any actions taken within threads are traceable and secure.

End to end encryption
At-Rest Encryption
Ensures that data transmitted between users and the server is encrypted, preventing unauthorized access.
Encrypts stored data (files, messages, designs) to protect it even if the storage medium is compromised.
IP and Intellectual Property Protection
Controlled Document Access: Protects intellectual property (IP) by allowing secure access only to users involved in specific projects or tasks.
On-Premise Hosting: Take full-control of your security measures and ensure that your IP and Intellectual is fully within your grasp.
Regular Security Audits and Updates
Vulnerability Assessments: Regularly tests the system for vulnerabilities and applies security patches or updates to address newly discovered risks.
Penetration Testing: Conducts regular testing to simulate cyber-attacks and ensure the robustness of the system against threats.
Let's get in touch
We'd love to hear about your current projects and how Authentise might help you achieve more. You can also simply book a demo with our team.

_edited.jpg)
.png)

.png)
.jpg)

.png)